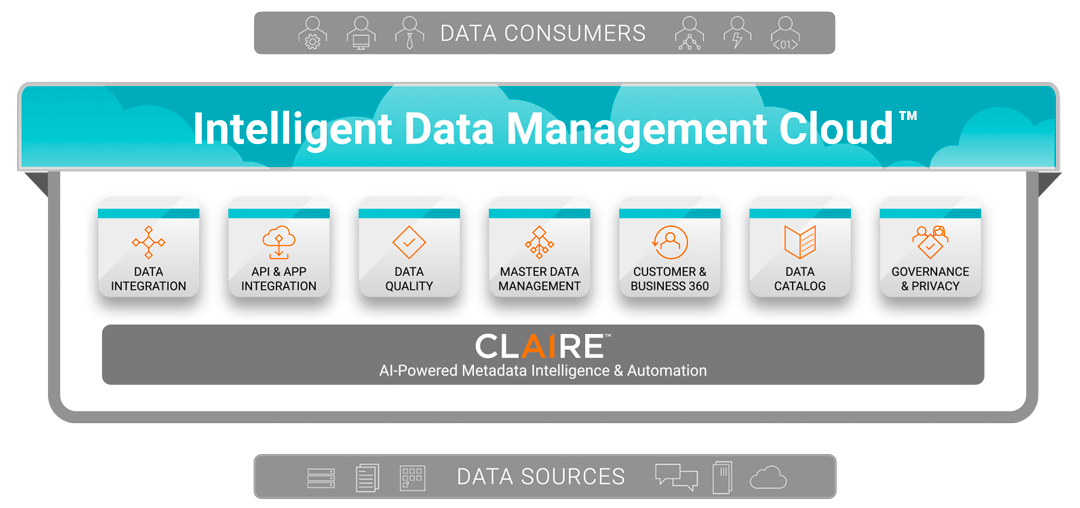
In this article, I will briefly mention about solutions brought by Informatica Intelligent Data Platform on data security and then try to provide you detailed information on data discovery and security analytics platform Informatica Secure@Source, which is an one of the priority issues especially on PoPD/GDPR one, and which offers a solution to this issue.
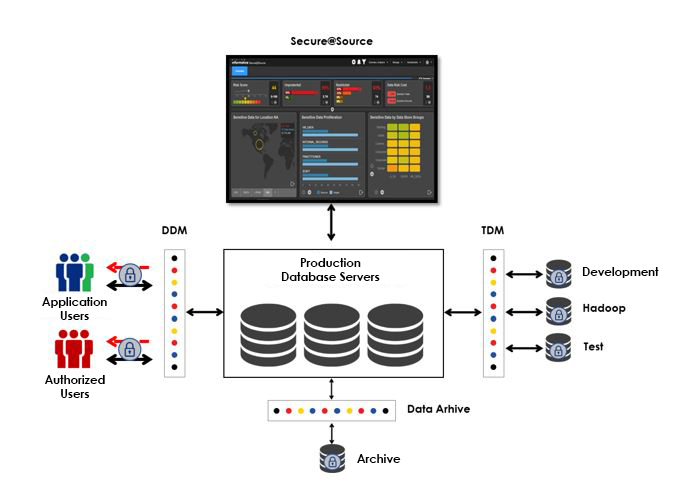
Data Security Solutions
The Informatica platform offers 4 different solutions for data security. If we briefly mention about these solutions;
Data Security Group
- Secure@Source (S@S)
Secure@Source performs the discovery of sensitive data in many different systems and risk scoring in particular of these systems.
- Dynamic Data Masking (DDM)
Dynamic Data Masking allows viewing of sensitive data only by authorized users by entering between users and applications a proxy application and by modifying user queries. The data is not transferred to any other medium and is dynamically masked on the source system. The data remains in the original form on the source system.
- Test Data Management (TDM)
Test Data Management enables data on live systems to be transferred to systems such as development or test environments. During this transfer, the relations between the tables and the meaning integrity of the data are preserved. Although sensitive data is masked, a subset of the data is transferred instead of the entire data in accordance with the determined business rules.
- Data Archive (DA)
Data Archive enables archiving of data on live systems in less costly environments. In this way, it is aimed to erase inactive data on live systems, increase the performance of operational systems and reduce costs.
Informatica Secure@Source
Informatica Secure@Source
As seen above, Informatica Secure@Source has a web-based screen, it also has following functions especially in line with PoPD/GDPR needs;
- Sensitive data detection and classification
- Dissemination analysis
- Anomaly detection
- Policy-based alarm
- Identification of high-risk systems
- Risk scoring
- Monitoring of user activity specific to sensitive data
- Precise data detection on structural and non-structural source systems
- Taking actions related to data masking, etc.
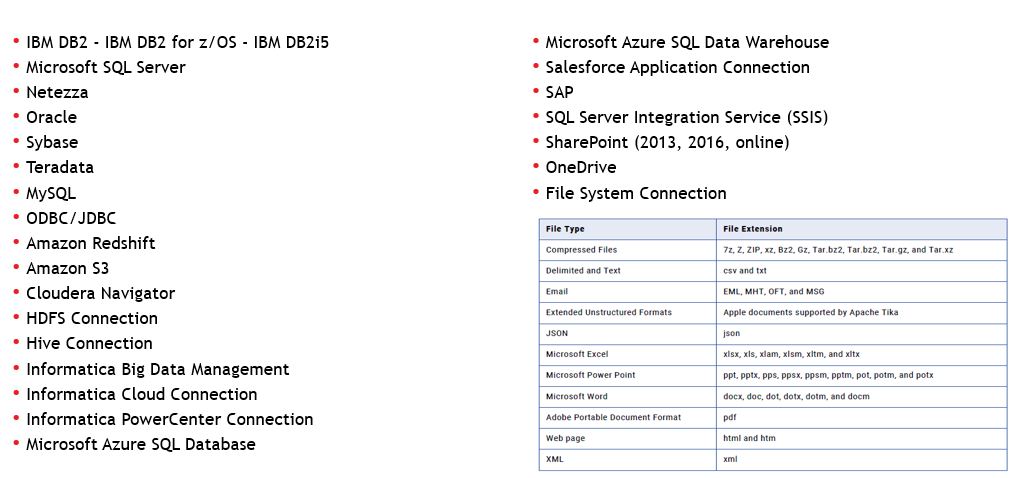
Data Stores
All systems that the Informatica Secure@Source solution provides access are called as “Data Store”. It provides access to many different systems (Application, Database, ETL, File System etc.) with the help of ready connectors and these systems are constantly expanding. Currently supported systems are as follows:
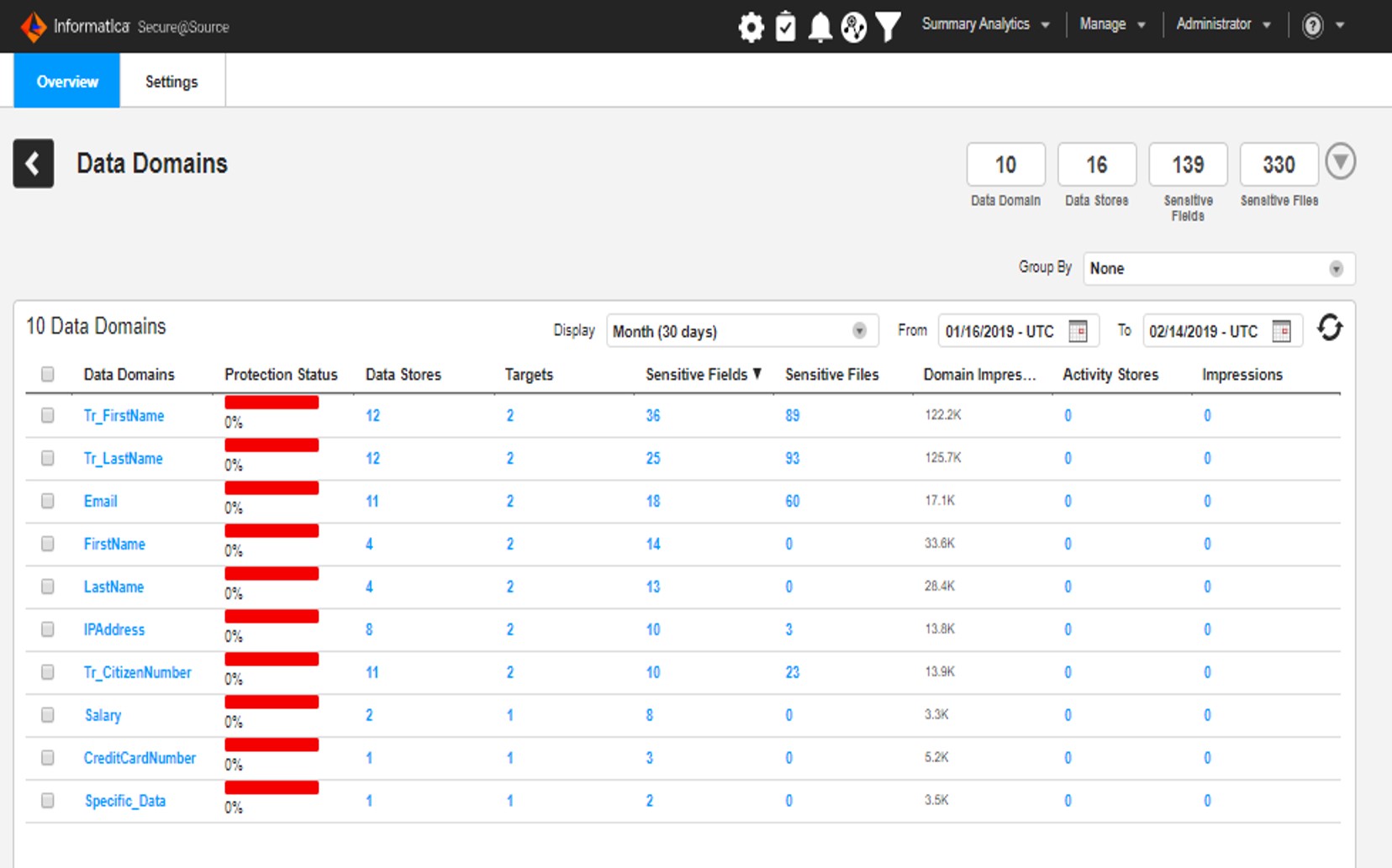
Data Domain Discovery
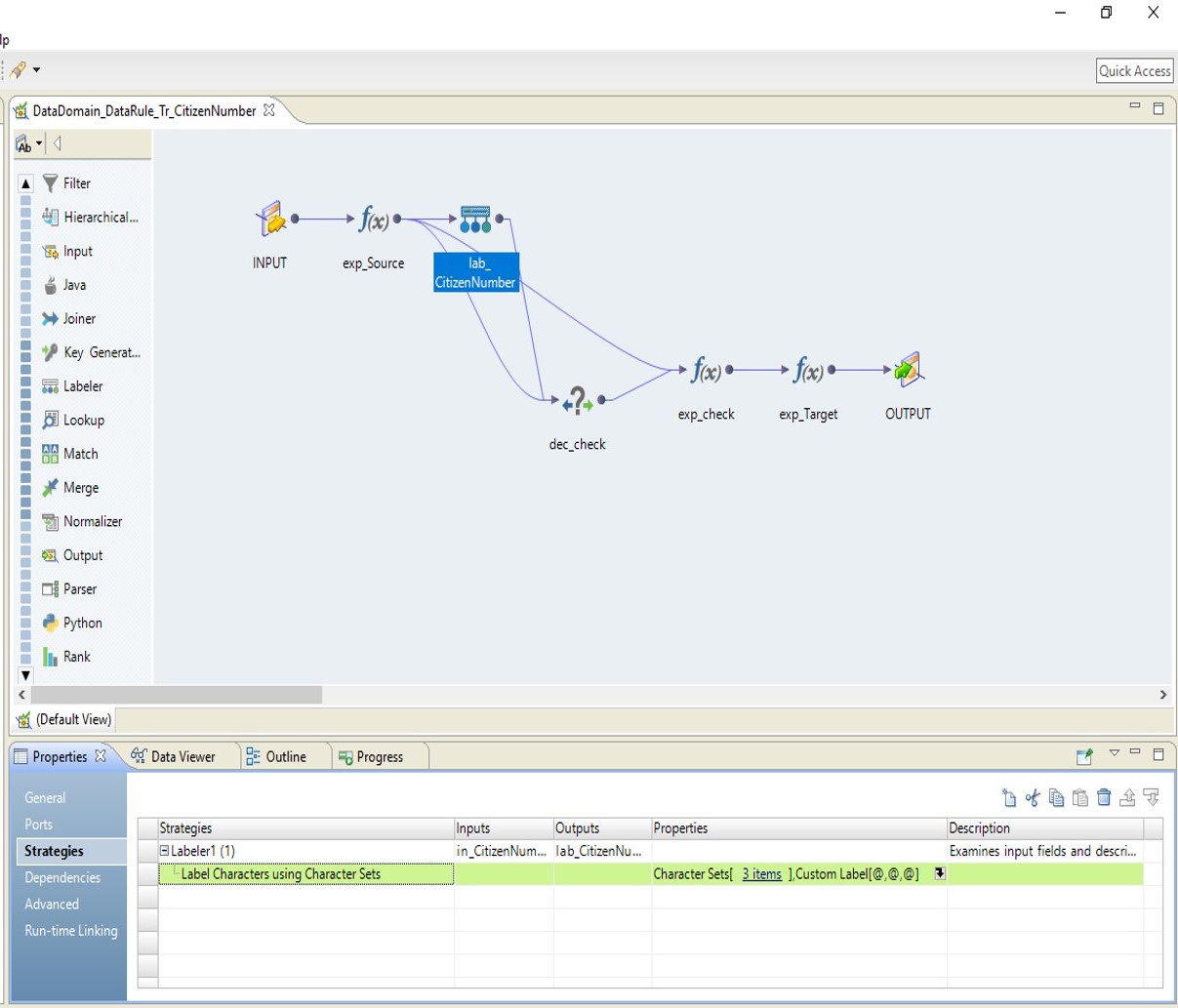
Data Domain Discovery is the discovery rules used for the detection of sensitive data on the access systems (Data Store). As well as many ready-made rules that come with the installation by Informatica, additional rules are developed according to the needs. And also, data discovery rules can be developed on web-based screens, and complex rules are developed with the help of drag and drop feature and rich transformations through screens called developers. The discovery of sensitive data is determined by making controls on both metadata and data.
Developer Tool
Classification
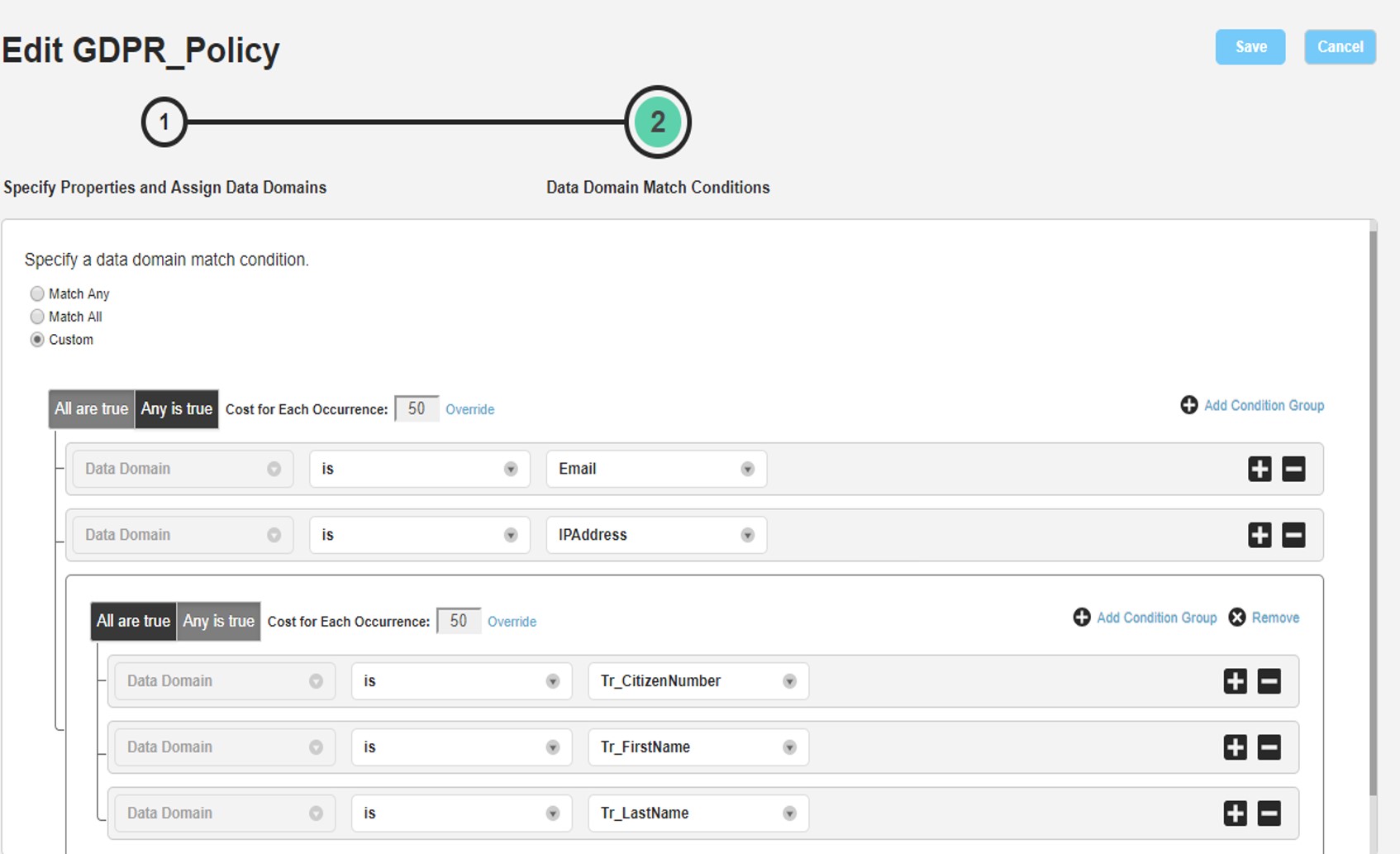
After developing data discovery rules, it is provided to classify the sensitive data detected on source systems. And within the relevant classification, different criteria such as “and” or “or” are given as required among data discovery rules. As can be seen in the example below, a policy called PR GDPR_Policy has been created and the data discovery rules under this policy have been selected according to various conditions.
Scan & Monitoring
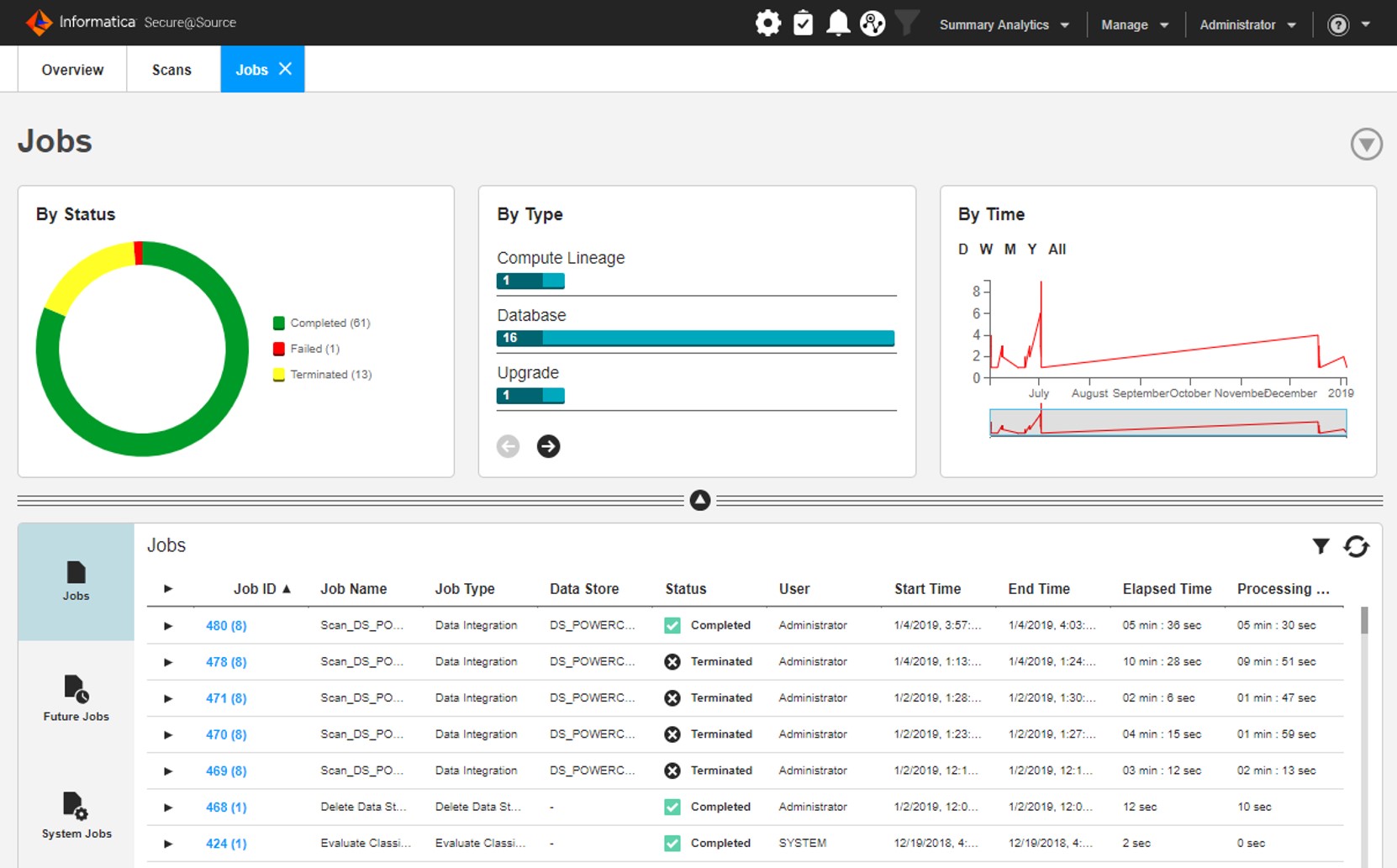
After Source systems have been identified (Data Store), data discovery rules (Data Domain Discovery) have been developed and the classification (Classification) definitions have been made, then the defining the relevant scan jobs (scan) and execution are provided. And all these scanning activities are monitored through the monitoring screens (Jobs). Informatica Secure@Source enables the performance of the scanning works related to its big in effective manner with its big data based architecture.
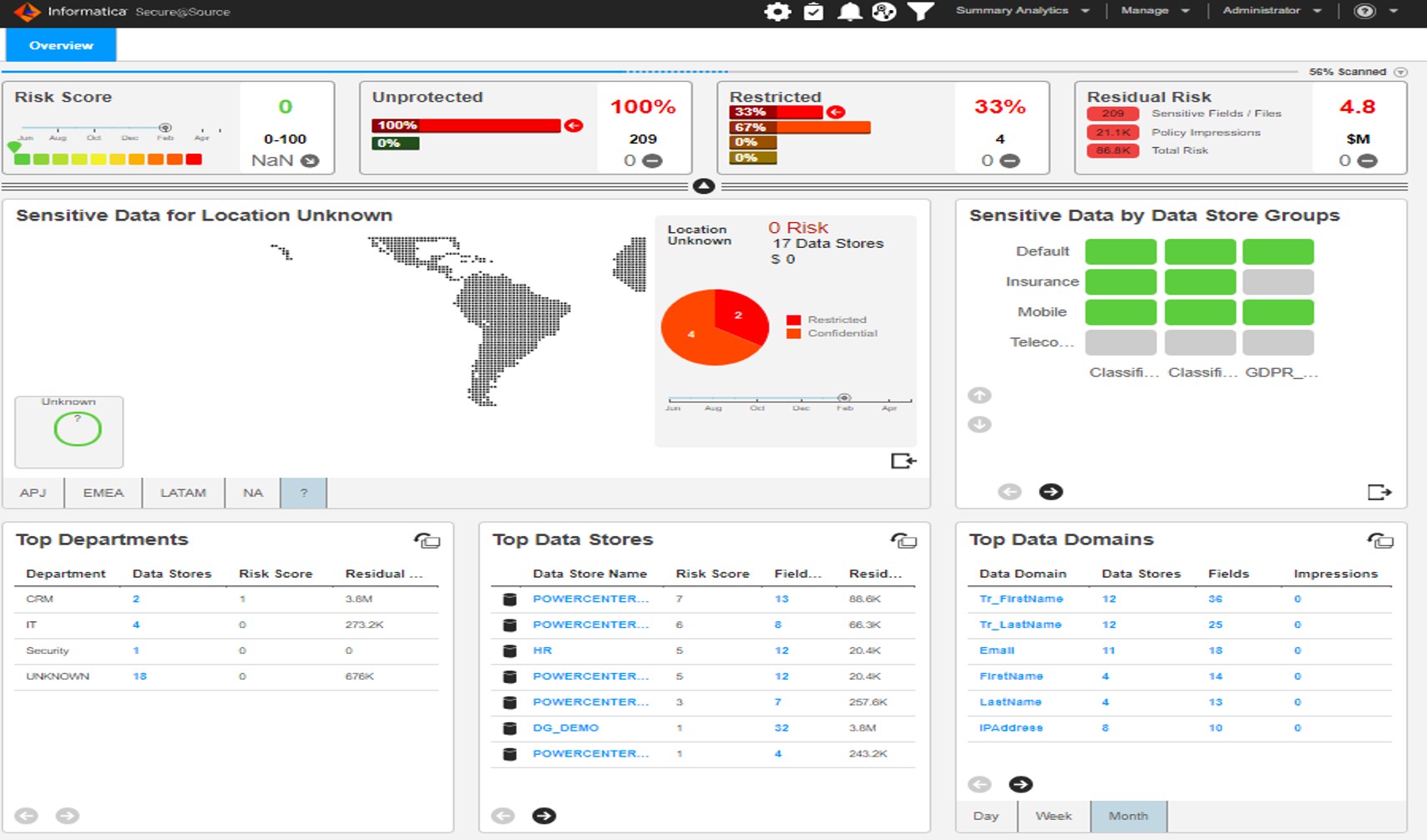
Dashboard
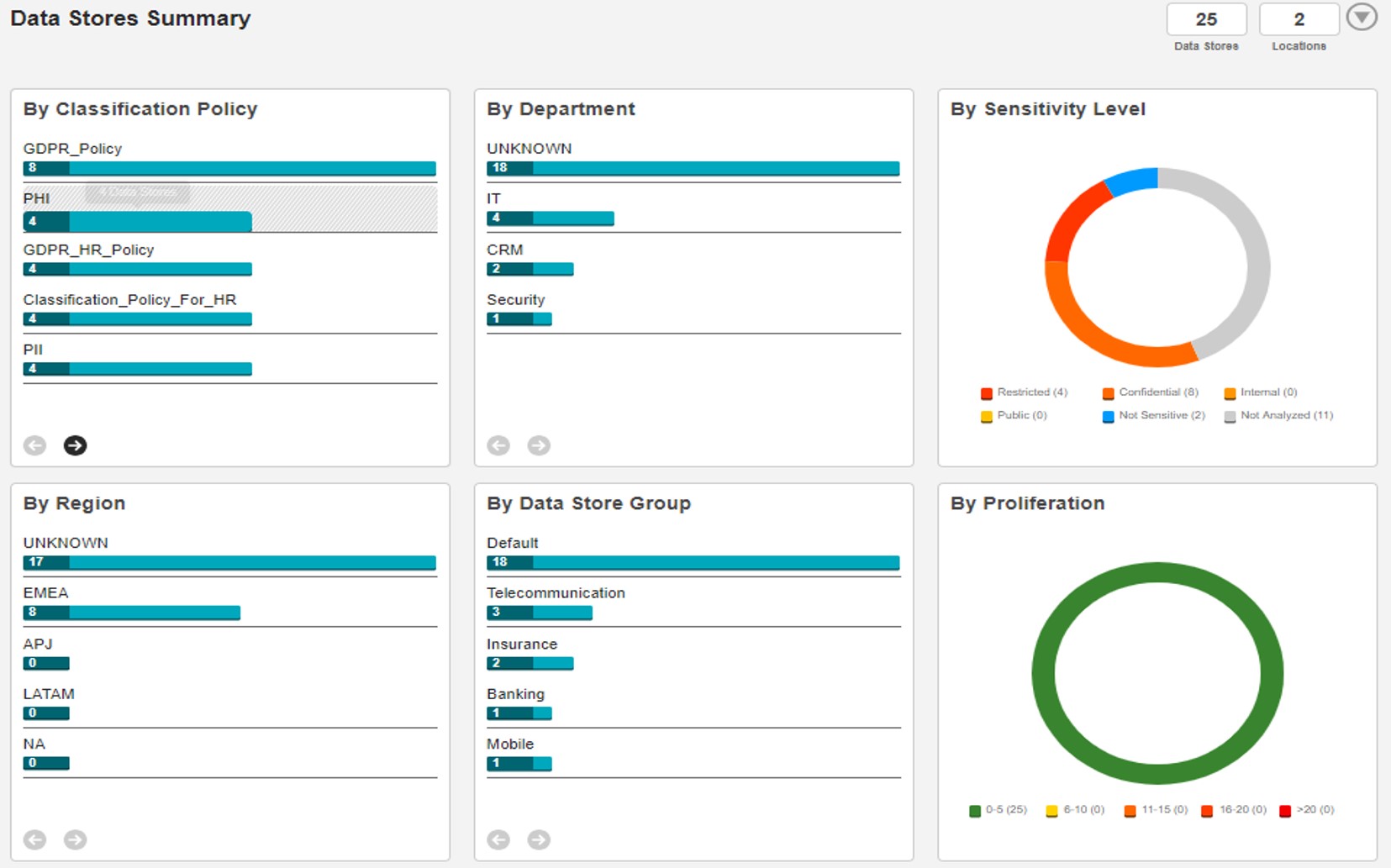
With the completion of the relevant scanning results, summarized or detailed reports (Location, Department, Region based) can be monitored through Informatica Secure@Source screens.
Summarized Reports
If desired, all results can also be accessed by external systems via ready-made services (Rest-Api).
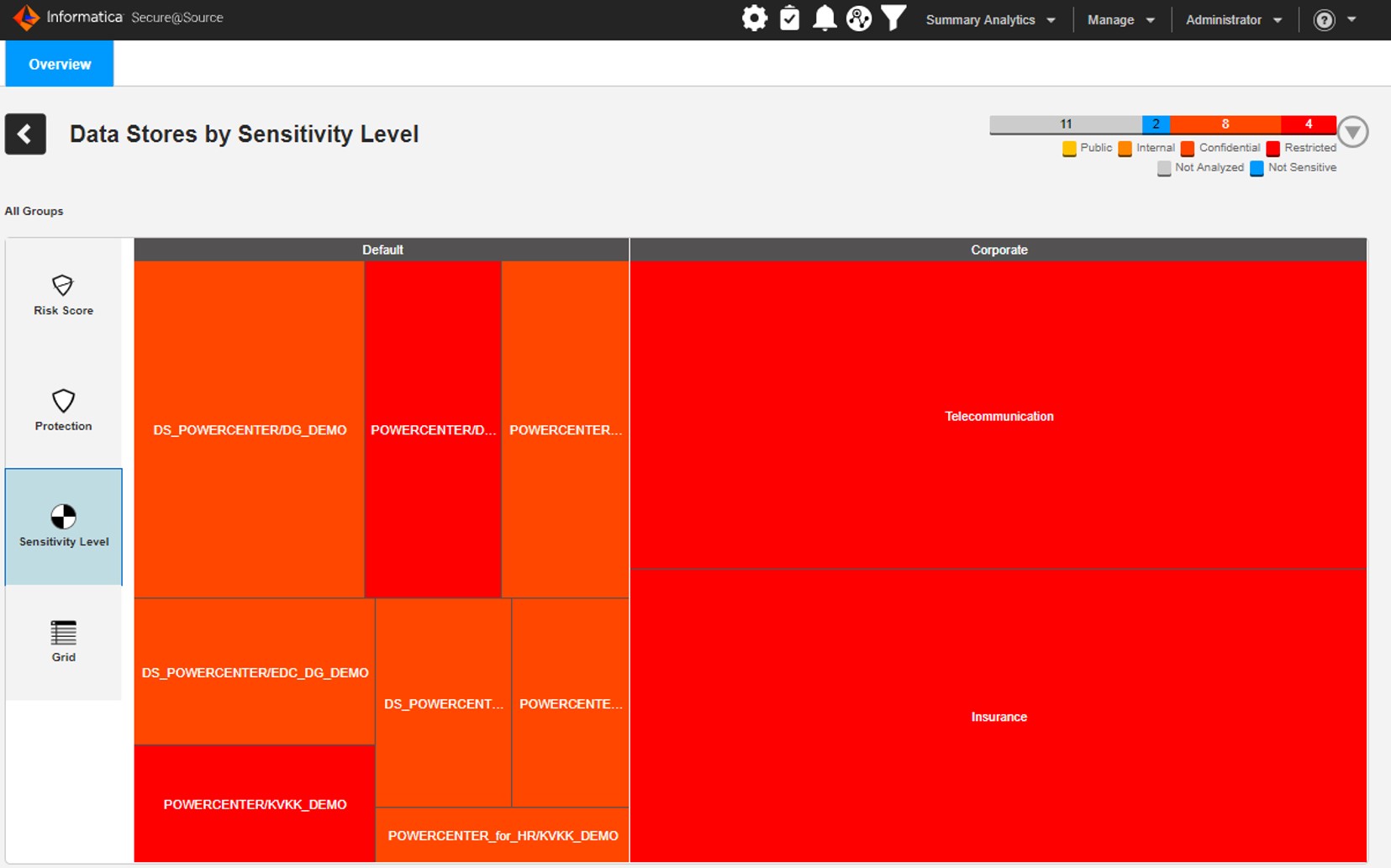
Risk Score Map
Detailed Statistics
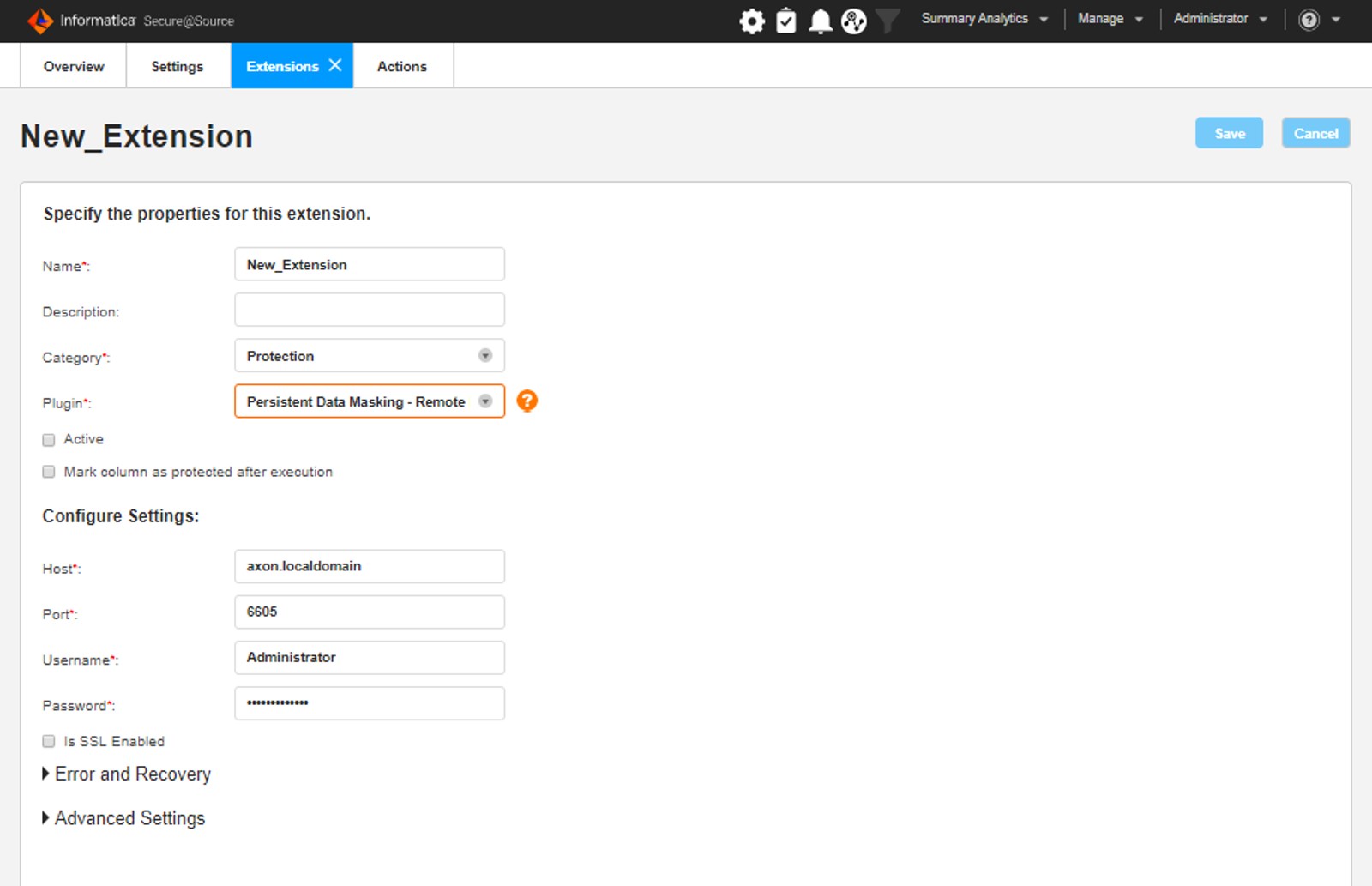
Action
Informatica Secure@Source also offers different capabilities for taking related actions after detecting sensitive data. (Triggering an external job, sending email to related users or masking sensitive data via Informatica security solutions etc.)
Taking Action
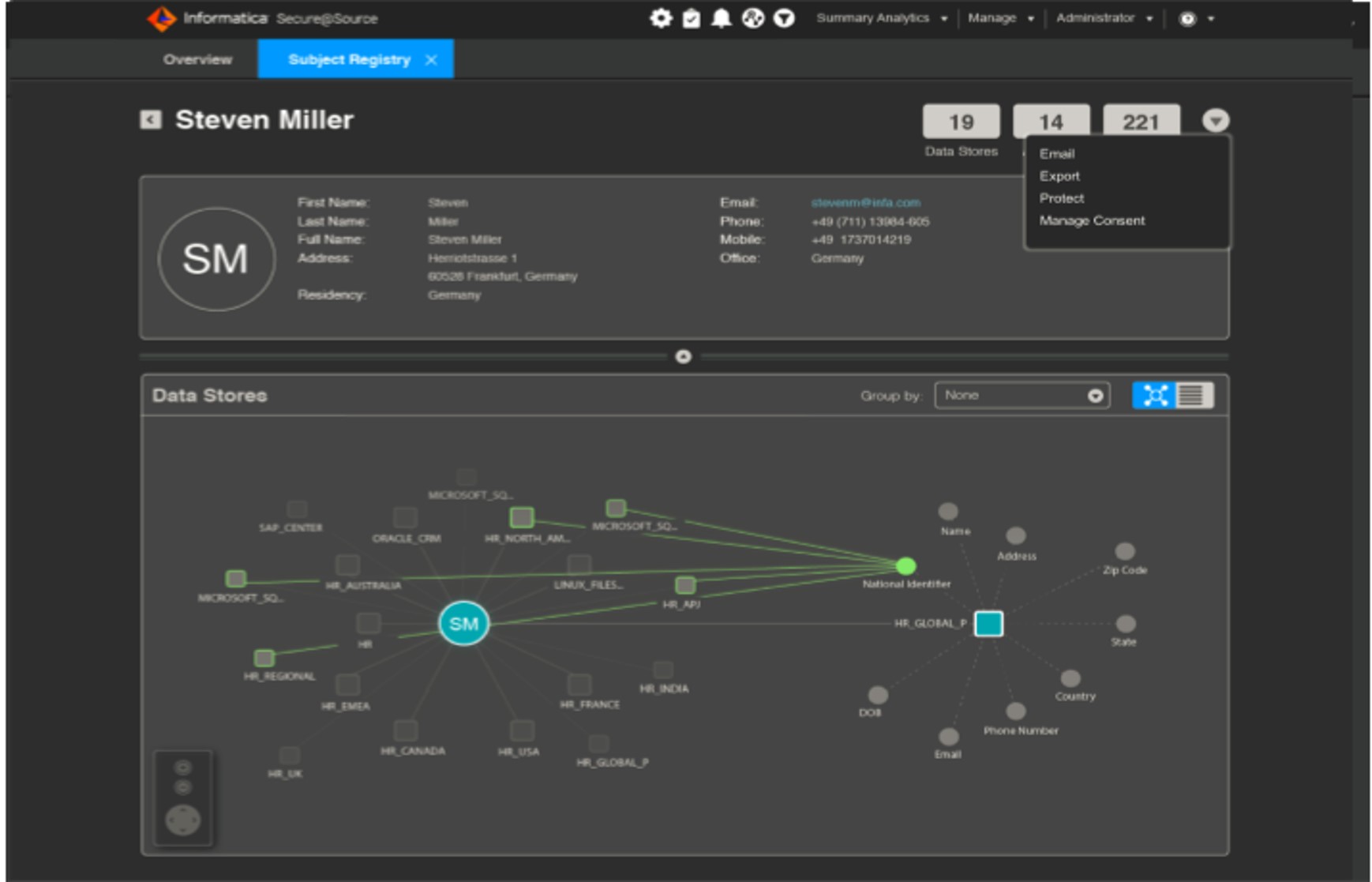
Subject Registry
In addition to the features, that I mentioned above, PoPD/ GDPR specific customer-based search and viewing of which data is in which system specific to scanned customers can be performed thanks to the feature called Registry Subject Registry.
Subject Registry
To sum up, Informatica Secure@Source provides an integrated data security platform throughout the organization, both in terms of KVKK/GDPR requirements and security requirements.
Evrim AY